添加 SSH 公钥指南
本文描述了在智算云平台的机器实例中添加你的 SSH 公钥。添加 SSH 公钥后,可在本地 SSH 远程登录智算云平台的机器实例(例如开发机、AICoder)。
注意
关于 SSH 原理介绍,建议参考阮一峰的 SSH 教程。
前提条件
请确保你可以登录智算云平台,可访问需要添加 SSH 公钥的机器实例。验证方式:
开发机:从开发机列表页点击登录,可打开 Web Terminal。
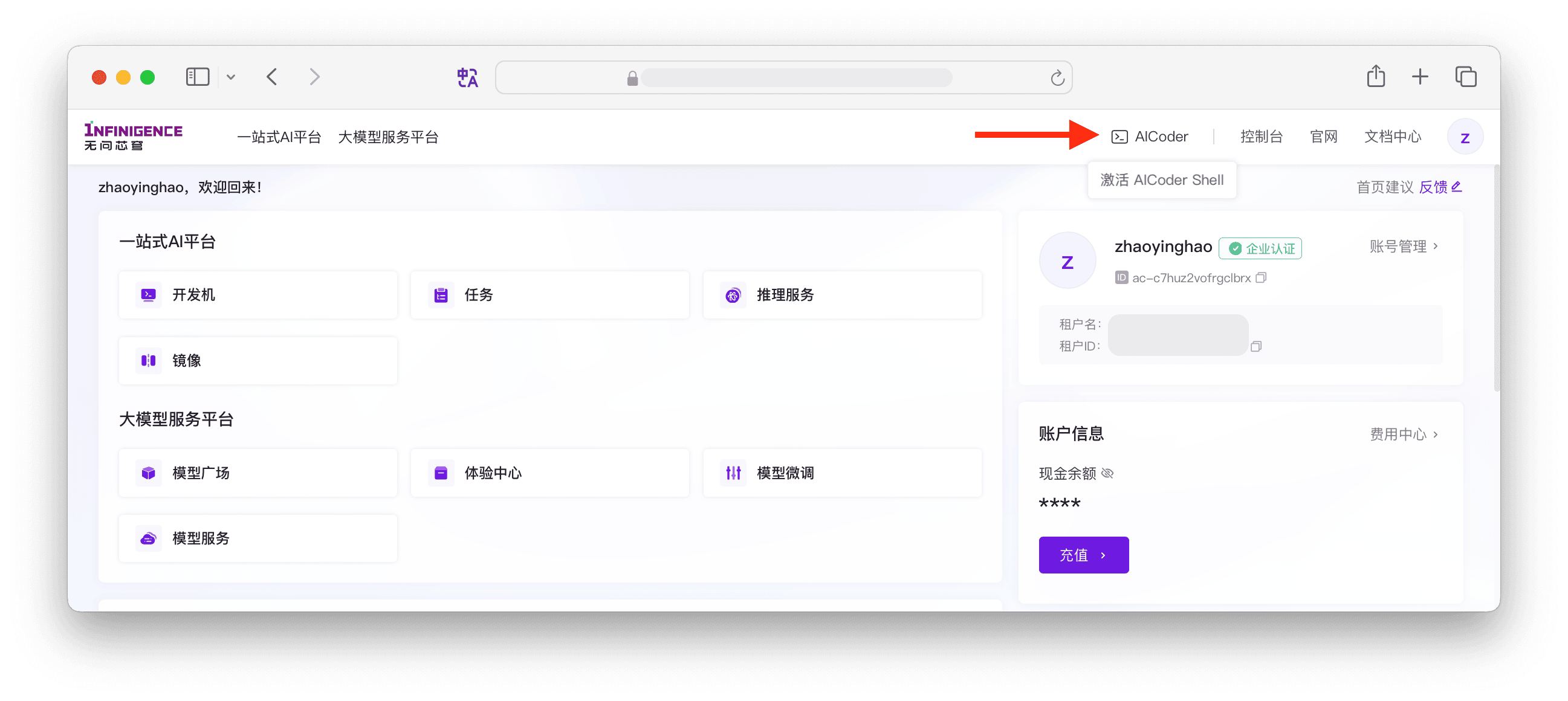
AICoder:点击智算云控制台顶部按钮激活 AICoder Shell。
注意
开发机和 AICoder 不支持用户名/密码认证进行 SSH 远程登录。因此,你需要登录智算云平台 Web 界面,在 Web 界面中操作添加 SSH 公钥。
获取 SSH 公钥
首先,我们先查看你的机器本地是否已存在 SSH 公钥。如果存在,可直接复用。
复制已有公钥
检查本地是否已存在 SSH 密钥对。
macOS/Linux
如果系统为 macOS/Linux,SSH 公钥通常存储在 ~/.ssh 目录下。文件名通常为 /id_rsa.pub 或 ~/.ssh/id_ed25519.pub。
# 列出 ~/.ssh 目录下的文件
ls -alt ~/.ssh
# 查看公钥文件的内容。请按需替换为 ~/.ssh/id_ed25519.pub
cat ~/.ssh/id_rsa.pub如上所示,请复制 cat 命令输出的内容(SSH 公钥)备用。
Windows
在 文件资源管理器 中打开
C:\Users\你的用户名\.ssh目录。- 如果存在
id_rsa.pub或id_ed25519.pub文件,则说明你已经拥有 SSH 公钥。 - 如果不存在以上文件,则需要按照以下步骤生成新的 SSH 密钥对。
- 如果存在
用文本编辑器打开
id_rsa.pub或id_ed25519.pub文件。复制文件中的所有内容。
生成新的 SSH 密钥对
如果本地没有 SSH 密钥对,则生成新的 SSH 密钥对。
macOS/Linux
打开 终端。如果需要生成新的 SSH 密钥对,请输入以下命令:
bash# 生成 rsa 类型的 SSH 密钥对。密钥验证速度较慢。广泛支持,几乎所有 SSH 客户端和服务器都支持。适用于需要广泛兼容性的场景。 ssh-keygen -t rsa -b 4096 -C "your_email@example.com" # 或者,生成 ed25519 类型的 SSH 密钥对。性能更好,密钥验证速度更快,计算效率高。 ssh-keygen -t ed25519 -C "your_email@example.com"将
your_email@example.com替换为你的电子邮件地址。警告
如果不熟悉 SSH 相关配置,在系统提示提示输入密钥文件名和密码时,直接按下回车键确认,使用默认值即可。
输入以下命令并回车,查看并复制 SSH 公钥内容:
bash# 查看 .pub 后缀的公钥文件内容 cat ~/.ssh/id_rsa.pub # 或者 cat ~/.ssh/id_ed25519.pub
Windows
如果需要生成新的 SSH 密钥对,建议先安装 Git Bash。打开 Git Bash,输入以下命令:
bash# 生成 rsa 类型的 SSH 密钥对。密钥验证速度较慢。广泛支持,几乎所有 SSH 客户端和服务器都支持。适用于需要广泛兼容性的场景。 ssh-keygen -t rsa -b 4096 -C "your_email@example.com" # 或者,生成 ed25519 类型的 SSH 密钥对。性能更好,密钥验证速度更快,计算效率高。 ssh-keygen -t ed25519 -C "your_email@example.com"将
your_email@example.com替换为你的电子邮件地址。警告
如果不熟悉 SSH 相关配置,在系统提示提示输入密钥文件名和密码时,直接按下回车键确认,使用默认值即可。
找到
.pub后缀的公钥文件,用文本编辑器打开,复制其中的所有内容。
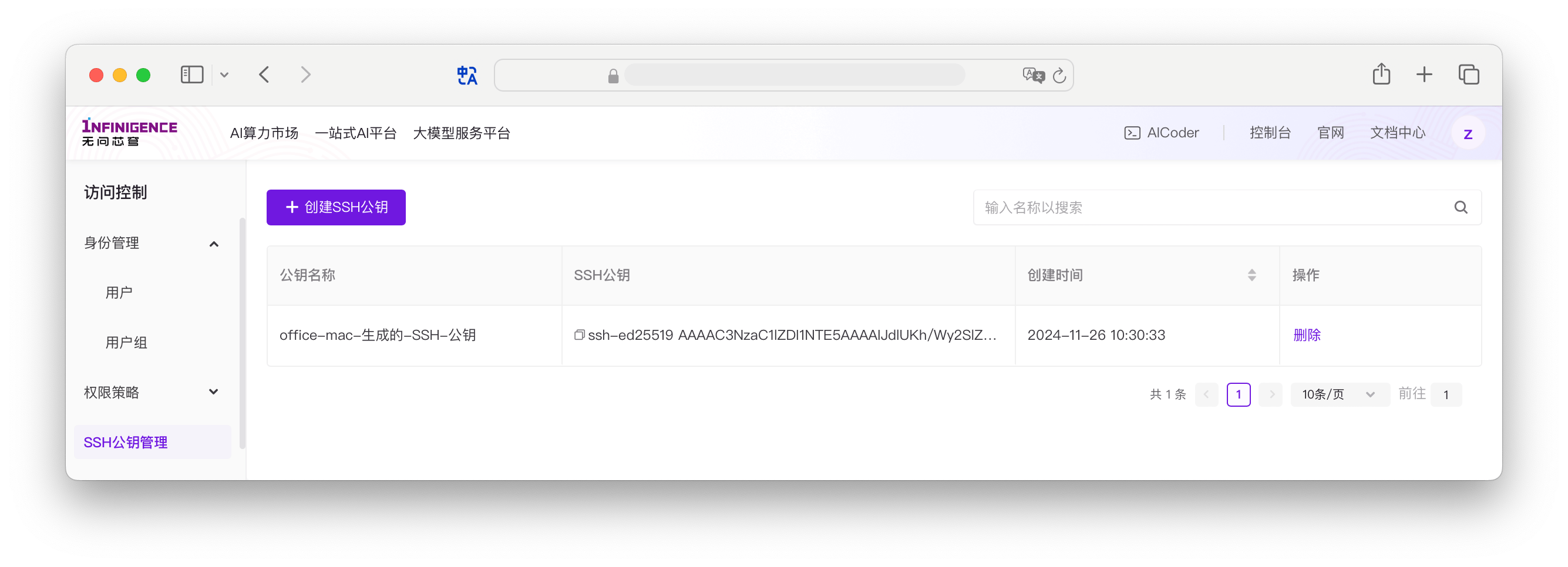
自动注入 SSH 公钥到机器实例
推荐使用智算云平台 SSH 公钥管理功能,由平台全局管理实例中的 SSH 公钥。在您的开发机或 AICoder 每次启动时,由平台检查 ~/.ssh/authorized_keys 文件,并自动注入您已添加的 SSH 公钥。
注意
- 对于运行中的实例,智算云平台 SSH 公钥的改动不会立即生效。如需立即生效,对开发请执行关闭、启动操作,对 AICoder 请执行一键重启。
- 如果不需要平台全局管理您的 SSH 公钥,可使用手动配置。您需要自行维护
~/.ssh/authorized_keys文件。
手动添加 SSH 公钥到机器实例
只要开发机或 AICoder 的 ~/.ssh/authorized_keys 文件中包含您的 SSH 公钥,即可通过密钥认证直接登录。
如果不使用智算云平台的 SSH 公钥管理功能,可在开发机或 AICoder 中手动修改 ~/.ssh/authorized_keys 文件,添加公钥,该修改即刻生效。手动修改将持久化保存在实例系统盘。
注意
- 如果改配开发机,且选择清空系统盘,手动修改将丢失。
- 如果一键重置 AICoder,将强行清空系统盘,手动修改将丢失。
将 SSH 公钥添加到现有开发机
如果你需要将 SSH 公钥添加到已创建的开发机,请按照以下步骤操作:
先登录智算云平台,通过登录按钮打开 Web Shell,再执行后续步骤。

确保
.ssh目录存在,如果不存在则创建:bashmkdir -p ~/.ssh将公钥内容添加到
authorized_keys文件中:bashecho "ssh-rsa AAAAB3NzaC1yc2E... your_email@example.com" >> ~/.ssh/authorized_keys将
ssh-rsa AAAAB3NzaC1yc2E... your_email@example.com替换为你在 获取 SSH 公钥 部分复制的公钥内容。- 如果
authorized_keys文件不存在,该命令会自动创建。 - 确保使用
>>将公钥内容追加到文件末尾,而不是覆盖原有内容。
你可能希望检查是否添加成功,请执行以下命令:
bash# 输出 authorized_keys 文件内容 cat ~/.ssh/authorized_keys- 如果
设置
authorized_keys文件的权限:bashchmod 600 ~/.ssh/authorized_keys这将确保只有你拥有该文件的读写权限。
将 SSH 公钥添加到 AICoder
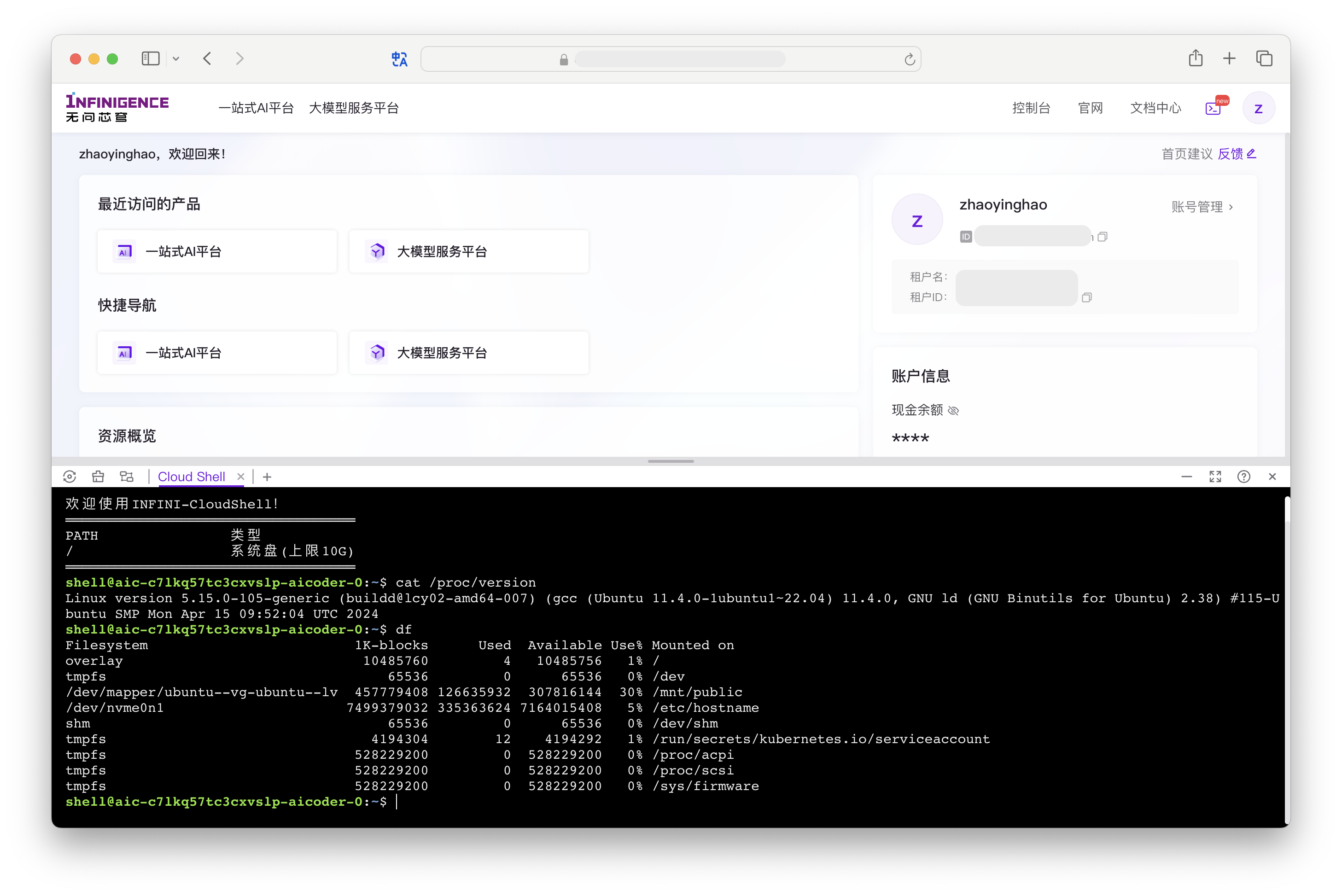
如果你需要将 SSH 公钥添加到 AICoder,必须打开 AICoder Shell,手动操作添加公钥。
登录智算云平台,打开 AICoder Shell,再执行后续步骤。
默认情况下,
.ssh目录已存在,如果不存在则创建:bashmkdir -p ~/.ssh将公钥内容添加到
authorized_keys文件中:bashecho "ssh-rsa AAAAB3NzaC1yc2E... your_email@example.com" >> ~/.ssh/authorized_keys将
ssh-rsa AAAAB3NzaC1yc2E... your_email@example.com替换为你在 获取 SSH 公钥 部分复制的公钥内容。- 如果
authorized_keys文件不存在,该命令会自动创建。 - 确保使用
>>将公钥内容追加到文件末尾,而不是覆盖原有内容。
你可能希望检查是否添加成功,请执行以下命令:
bash# 输出 authorized_keys 文件内容 cat ~/.ssh/authorized_keys- 如果
设置
authorized_keys文件的权限:bashchmod 600 ~/.ssh/authorized_keys这将确保只有你拥有该文件的读写权限。
测试 SSH 连接
完成以上步骤后,你就可以尝试使用 SSH 公钥登录到你的实例了。
登录开发机
前往智算云平台获取开发机 SSH 登录命令,包含远程服务器的用户名、IP地址、和端口号。注意,不支持默认 22 端口号。
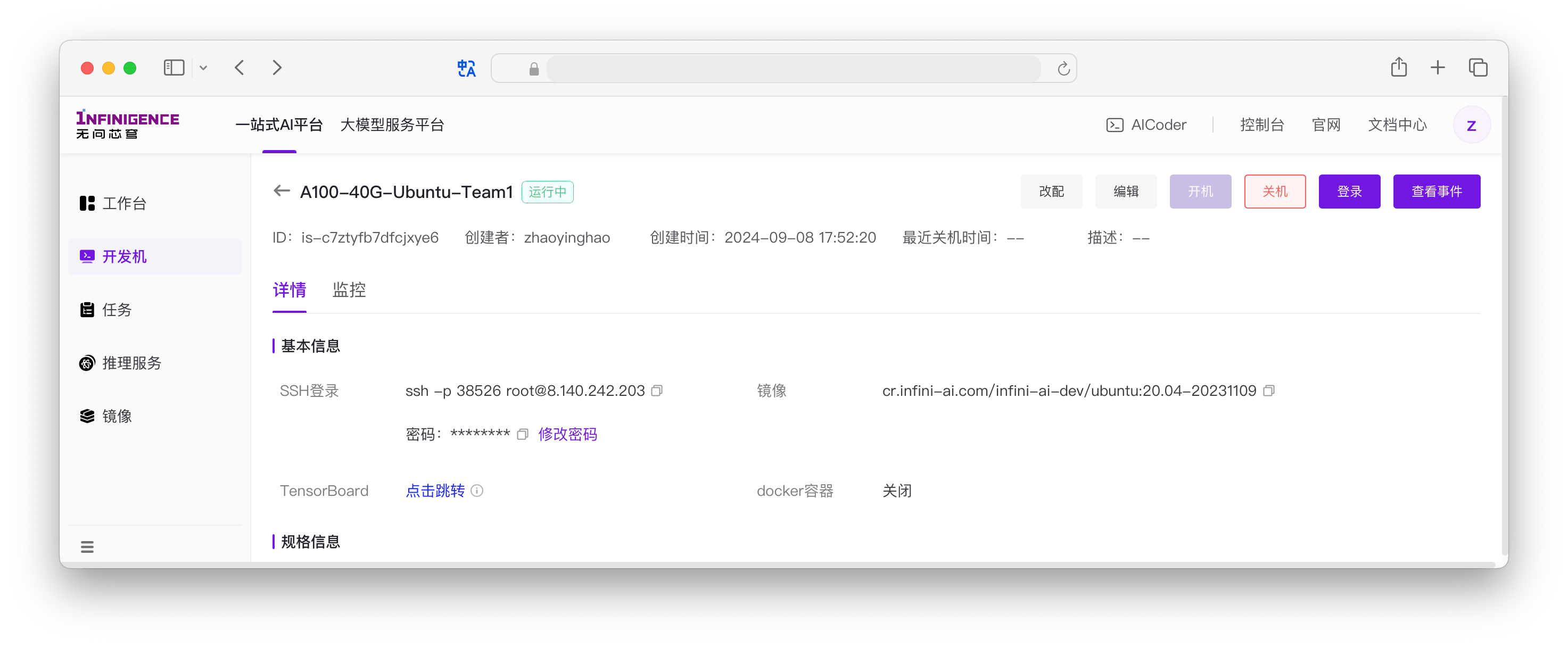
例如,如果开发机的 SSH 端口是 41587,则可以使用以下命令登录:
ssh -p 41587 username@your_server_ip如果一切配置正确,你应该可以直接登录到开发机,无需输入密码。
登录 AICoder
AICoder 需要通过智算云平台提供的跳板机访问。在打开 AICoder Shell 后,在窗口右上角点击密钥按钮,从弹窗可一键复制 AICoder SSH 连接命令:
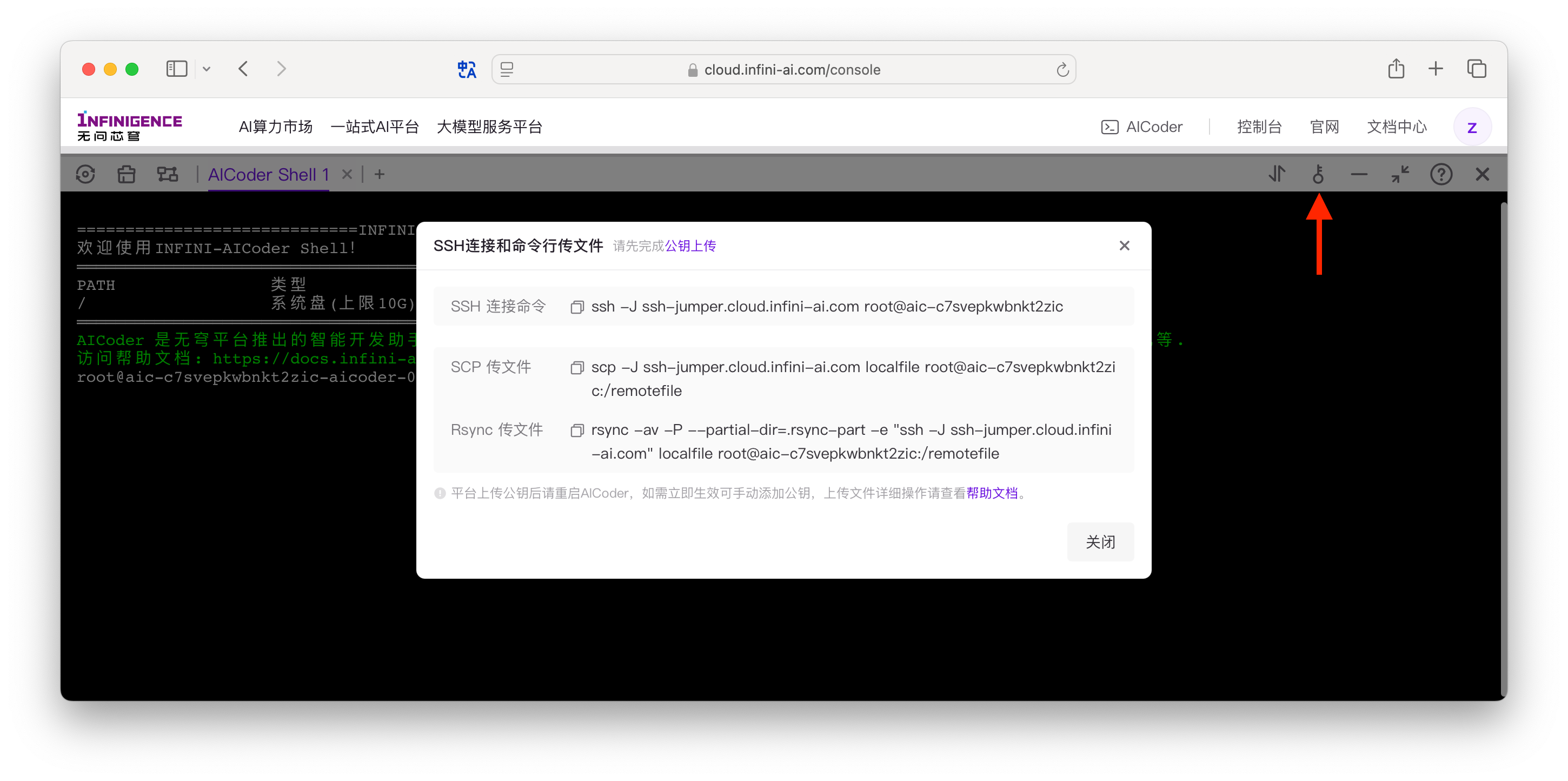
如需帮助,请参考文档: 在本地连接到 AICoder Shell。
无法建立 SSH 远程连接
一般为本地特殊配置问题造成,请检查以下事项:
检查本地是否存在多个命令行环境(例如 Windows 的 CMD/PowerShell/GitBash )。
注意
不同的命令行环境和 SSH 客户端可能使用的 SSH 密钥存放路径不一样。你需要自行确认当前 SSH 客户端使用的 SSH 公私钥文件路径,并确保在智算云平台上传了当前密钥文件路径下的公钥(
.pub)文件内容。检查是否使用了非默认的密钥文件名,导致本地 SSH 客户端无法找到正确的密钥对。
注意
默认的 SSH 私钥名称包括
id_rsa、id_dsa、id_ecdsa、id_ed25519和id_xmss,每个对应的公钥名称分别是id_rsa.pub、id_dsa.pub、id_ecdsa.pub、id_ed25519.pub和id_xmss.pub。这些密钥对通常存储在用户主目录的.ssh目录中,并在通过 SSH 连接到远程服务器时用于公钥认证。如果这些密钥不存在,SSH 将找不到用于认证的默认密钥,可能会导致 “Permission denied (publickey)” 错误。如果必须使用非默认密钥文件名,可自行在本地 SSH 配置文件(
.ssh/config)中添加 SSH alias,并配置IdentityFile,指定 SSH 私钥文件路径,例如:# 用于连接开发机的 SSH alias 配置模板 Host name-of-ssh-host-here HostName host-fqdn-or-ip-goes-here User root IdentitiesOnly Yes # 如果使用了非默认的 SSH 私钥文件,请务必确保私钥文件权限符合要求(可对私钥文件执行 `chmod 600`),并在配置中指定私钥文件路径。 # 配置模版 2 Host aicoder HostName aic-c8lkg5b88mieqw6b User root IdentitiesOnly Yes IdentityFile ~/.ssh/custom_private_key# 用于连接 AICoder 的 SSH alias # 配置模板 1 Host aicoder HostName aic-c8lkg5b88mieqw6b User root IdentitiesOnly Yes ProxyJump ssh-jumper.cloud.infini-ai.com # 如果使用了非默认的 SSH 私钥文件,请务必确保私钥文件权限符合要求(可对私钥文件执行 `chmod 600`),并在配置中指定私钥文件路径。 # 配置模版 2 Host aicoder HostName aic-c8lkg5b88mieqw6b User root IdentitiesOnly Yes IdentityFile ~/.ssh/custom_private_key ProxyJump ssh-jumper.cloud.infini-ai.com可以在
ssh命令中增加-v命令来获取 debug 信息,例如:bash# 连接开发机时,输出 debug 信息 ssh -v -p 41587 username@your_server_ip # 连接 AICoder 时,输出 debug 信息 ssh -v -J ssh-jumper.cloud.infini-ai.com username@aicoder_id你可以将以上输出的 debug 信息提供给无问芯穹,由我们协助排除问题。
点我查看 debug 输出示例
OpenSSH_9.6p1, LibreSSL 3.3.6 debug1: Reading configuration data /Users/janedoe/.ssh/config debug1: /Users/janedoe/.ssh/config line 1: Applying options for aic-c7svepkwbnkt2zic debug1: Reading configuration data /etc/ssh/ssh_config debug1: /etc/ssh/ssh_config line 21: include /etc/ssh/ssh_config.d/* matched no files debug1: /etc/ssh/ssh_config line 54: Applying options for * debug1: Setting implicit ProxyCommand from ProxyJump: ssh -v -W '[%h]:%p' ssh-jumper.cloud.infini-ai.com debug1: Authenticator provider $SSH_SK_PROVIDER did not resolve; disabling debug1: Executing proxy command: exec ssh -v -W '[aic-c7svepkwbnkt2zic]:22' ssh-jumper.cloud.infini-ai.com debug1: identity file /Users/janedoe/.ssh/id_rsa type -1 debug1: identity file /Users/janedoe/.ssh/id_rsa-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa_sk type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa_sk-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519 type 3 debug1: identity file /Users/janedoe/.ssh/id_ed25519-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519_sk type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519_sk-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_xmss type -1 debug1: identity file /Users/janedoe/.ssh/id_xmss-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_dsa type -1 debug1: identity file /Users/janedoe/.ssh/id_dsa-cert type -1 debug1: Local version string SSH-2.0-OpenSSH_9.6 OpenSSH_9.6p1, LibreSSL 3.3.6 debug1: Reading configuration data /Users/janedoe/.ssh/config debug1: Reading configuration data /etc/ssh/ssh_config debug1: /etc/ssh/ssh_config line 21: include /etc/ssh/ssh_config.d/* matched no files debug1: /etc/ssh/ssh_config line 54: Applying options for * debug1: Authenticator provider $SSH_SK_PROVIDER did not resolve; disabling debug1: Connecting to ssh-jumper.cloud.infini-ai.com port 22. debug1: Connection established. debug1: identity file /Users/janedoe/.ssh/id_rsa type -1 debug1: identity file /Users/janedoe/.ssh/id_rsa-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa_sk type -1 debug1: identity file /Users/janedoe/.ssh/id_ecdsa_sk-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519 type 3 debug1: identity file /Users/janedoe/.ssh/id_ed25519-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519_sk type -1 debug1: identity file /Users/janedoe/.ssh/id_ed25519_sk-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_xmss type -1 debug1: identity file /Users/janedoe/.ssh/id_xmss-cert type -1 debug1: identity file /Users/janedoe/.ssh/id_dsa type -1 debug1: identity file /Users/janedoe/.ssh/id_dsa-cert type -1 debug1: Local version string SSH-2.0-OpenSSH_9.6 debug1: Remote protocol version 2.0, remote software version Go debug1: compat_banner: no match: Go debug1: Authenticating to ssh-jumper.cloud.infini-ai.com:22 as 'janedoe' debug1: load_hostkeys: fopen /Users/janedoe/.ssh/known_hosts2: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory debug1: SSH2_MSG_KEXINIT sent debug1: SSH2_MSG_KEXINIT received debug1: kex: algorithm: curve25519-sha256 debug1: kex: host key algorithm: rsa-sha2-512 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none debug1: expecting SSH2_MSG_KEX_ECDH_REPLY debug1: SSH2_MSG_KEX_ECDH_REPLY received debug1: Server host key: ssh-rsa SHA256:O2hm+ZEbGX70oLfhh+yojHcLIrv8T0cMNj4hOm//TZY debug1: load_hostkeys: fopen /Users/janedoe/.ssh/known_hosts2: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory debug1: Host 'ssh-jumper.cloud.infini-ai.com' is known and matches the RSA host key. debug1: Found key in /Users/janedoe/.ssh/known_hosts:30 debug1: ssh_packet_send2_wrapped: resetting send seqnr 3 debug1: rekey out after 134217728 blocks debug1: SSH2_MSG_NEWKEYS sent debug1: expecting SSH2_MSG_NEWKEYS debug1: ssh_packet_read_poll2: resetting read seqnr 3 debug1: SSH2_MSG_NEWKEYS received debug1: rekey in after 134217728 blocks debug1: SSH2_MSG_EXT_INFO received debug1: kex_ext_info_client_parse: server-sig-algs=<ssh-ed25519,sk-ssh-ed25519@openssh.com,sk-ecdsa-sha2-nistp256@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,rsa-sha2-256,rsa-sha2-512,ssh-rsa,ssh-dss> debug1: kex_ext_info_check_ver: ping@openssh.com=<0> debug1: SSH2_MSG_SERVICE_ACCEPT received debug1: Authentications that can continue: publickey debug1: Next authentication method: publickey debug1: get_agent_identities: bound agent to hostkey debug1: get_agent_identities: ssh_fetch_identitylist: agent contains no identities debug1: Will attempt key: /Users/janedoe/.ssh/id_rsa debug1: Will attempt key: /Users/janedoe/.ssh/id_ecdsa debug1: Will attempt key: /Users/janedoe/.ssh/id_ecdsa_sk debug1: Will attempt key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI debug1: Will attempt key: /Users/janedoe/.ssh/id_ed25519_sk debug1: Will attempt key: /Users/janedoe/.ssh/id_xmss debug1: Will attempt key: /Users/janedoe/.ssh/id_dsa debug1: Trying private key: /Users/janedoe/.ssh/id_rsa debug1: Trying private key: /Users/janedoe/.ssh/id_ecdsa debug1: Trying private key: /Users/janedoe/.ssh/id_ecdsa_sk debug1: Offering public key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI debug1: Server accepts key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI Authenticated to ssh-jumper.cloud.infini-ai.com ([39.105.184.231]:22) using "publickey". debug1: channel_connect_stdio_fwd: aic-c7svepkwbnkt2zic:22 debug1: channel 0: new stdio-forward [stdio-forward] (inactive timeout: 0) debug1: Entering interactive session. debug1: pledge: filesystem debug1: Remote protocol version 2.0, remote software version OpenSSH_8.9p1 Ubuntu-3ubuntu0.10 debug1: compat_banner: match: OpenSSH_8.9p1 Ubuntu-3ubuntu0.10 pat OpenSSH* compat 0x04000000 debug1: Authenticating to aic-c7svepkwbnkt2zic:22 as 'zhaoyinghao' debug1: load_hostkeys: fopen /Users/janedoe/.ssh/known_hosts2: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory debug1: SSH2_MSG_KEXINIT sent debug1: SSH2_MSG_KEXINIT received debug1: kex: algorithm: sntrup761x25519-sha512@openssh.com debug1: kex: host key algorithm: rsa-sha2-512 debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none debug1: expecting SSH2_MSG_KEX_ECDH_REPLY debug1: SSH2_MSG_KEX_ECDH_REPLY received debug1: Server host key: ssh-rsa SHA256:zHeJT5X018HH5VXc0hiD+q+OF6dZyHUGpfY1xladT0I debug1: load_hostkeys: fopen /Users/janedoe/.ssh/known_hosts2: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts: No such file or directory debug1: load_hostkeys: fopen /etc/ssh/ssh_known_hosts2: No such file or directory debug1: Host 'aic-c7svepkwbnkt2zic' is known and matches the RSA host key. debug1: Found key in /Users/janedoe/.ssh/known_hosts:32 debug1: ssh_packet_send2_wrapped: resetting send seqnr 3 debug1: rekey out after 134217728 blocks debug1: SSH2_MSG_NEWKEYS sent debug1: expecting SSH2_MSG_NEWKEYS debug1: ssh_packet_read_poll2: resetting read seqnr 3 debug1: SSH2_MSG_NEWKEYS received debug1: rekey in after 134217728 blocks debug1: SSH2_MSG_EXT_INFO received debug1: kex_ext_info_client_parse: server-sig-algs=<ssh-ed25519,sk-ssh-ed25519@openssh.com,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ecdsa-sha2-nistp256@openssh.com,webauthn-sk-ecdsa-sha2-nistp256@openssh.com> debug1: kex_ext_info_check_ver: publickey-hostbound@openssh.com=<0> debug1: SSH2_MSG_SERVICE_ACCEPT received debug1: Authentications that can continue: publickey debug1: Next authentication method: publickey debug1: get_agent_identities: bound agent to hostkey debug1: get_agent_identities: ssh_fetch_identitylist: agent contains no identities debug1: Will attempt key: /Users/janedoe/.ssh/id_rsa debug1: Will attempt key: /Users/janedoe/.ssh/id_ecdsa debug1: Will attempt key: /Users/janedoe/.ssh/id_ecdsa_sk debug1: Will attempt key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI debug1: Will attempt key: /Users/janedoe/.ssh/id_ed25519_sk debug1: Will attempt key: /Users/janedoe/.ssh/id_xmss debug1: Will attempt key: /Users/janedoe/.ssh/id_dsa debug1: Trying private key: /Users/janedoe/.ssh/id_rsa debug1: Trying private key: /Users/janedoe/.ssh/id_ecdsa debug1: Trying private key: /Users/janedoe/.ssh/id_ecdsa_sk debug1: Offering public key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI debug1: Server accepts key: /Users/janedoe/.ssh/id_ed25519 ED25519 SHA256:p7MOitYza8BNXb9I5B+CEHeLO3jmN4WxNnHbvai2NLI Authenticated to aic-c7svepkwbnkt2zic (via proxy) using "publickey". debug1: channel 0: new session [client-session] (inactive timeout: 0) debug1: Requesting no-more-sessions@openssh.com debug1: Entering interactive session. debug1: pledge: filesystem debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0 debug1: client_input_hostkeys: searching /Users/janedoe/.ssh/known_hosts for aic-c7svepkwbnkt2zic / (none) debug1: client_input_hostkeys: searching /Users/janedoe/.ssh/known_hosts2 for aic-c7svepkwbnkt2zic / (none) debug1: client_input_hostkeys: hostkeys file /Users/janedoe/.ssh/known_hosts2 does not exist debug1: client_input_hostkeys: no new or deprecated keys from server debug1: Remote: /home/zhaoyinghao/.ssh/authorized_keys:1: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding debug1: Remote: /home/zhaoyinghao/.ssh/authorized_keys:1: key options: agent-forwarding port-forwarding pty user-rc x11-forwarding debug1: Sending environment. debug1: channel 0: setting env LC_TERMINAL_VERSION = "3.5.3" debug1: channel 0: setting env LANG = "zh_CN.UTF-8" debug1: channel 0: setting env LC_TERMINAL = "iTerm2" debug1: pledge: fork
非本地 SSH 客户端配置造成的情况:
AICoder 已被重置。如果您上次添加 SSH 公钥后一键重置过 AICoder,请注意 AICoder 的本地数据将被清空。请重新登录 AICoder,添加 SSH 公钥。
SSH 客户端所在网络的防火墙阻止了 SSH 连接。请与您的网络管理员联系,确认是否允许 SSH 连接,或是否开放了必要端口。
由于智算云平台的开发机可能基于不同的镜像构建,其支持的 SSH 密钥类型可能有限。请登录开发机,使用
cat /etc/ssh/sshd_config检查 SSH 服务端配置,检查HostKey类型的支持情况。# /etc/ssh/sshd_config # 以下配置表示支持 3 种 SSH 密钥类型 HostKey /etc/ssh/ssh_host_rsa_key HostKey /etc/ssh/ssh_host_ecdsa_key HostKey /etc/ssh/ssh_host_ed25519_key
注意事项
- 妥善保管你的私钥,不要将私钥泄露给任何人。
- 如果你的私钥丢失或被盗,请立即更换新的 SSH 密钥对,并更新智算云平台上的公钥。
参考资料
- 阮一峰 SSH 教程:SSH 密钥登录